Introduction
It is possible to log into an Azure VM using an Entra based identity. If you are using Bastion to access VMs and you would like to use an Entra ID, then you must use the Windows native client.
There are many reasons as to why you might want to authenticate to VMs using Entra. This may include:
- Not having Active Directory Domain services available.
- You are not utilising Entra domain services.
For the purpose of this article there are two types of Entra identities:
- Cloud-only: An account that is created in Entra and is not being synced to an on-premises Active Directory.
- Hybrid: An account that was created in an on-premises Active Directory and is being synced to Entra.
It is possible to utilise Bastion to RDP using both types of identities. This article will cover the necessary prerequisites for configuring Bastion for Entra authentication and provide resolutions to a couple of key issues.
Prerequisites
There are a number of prerequisites which must be followed before trying to connect to the VM. I won’t cover the low level details, as Microsoft have already done a good job with documenting these:
- Configure Bastion for native client connections
- Install the latest az modules using PowerShell.
- Follow the instructions stated in this article: Sign in to a Windows virtual machine in Azure by using Microsoft Entra ID including passwordless.
- Follow the instructions stated in this article: Connect to a VM using Bastion and the Windows native client
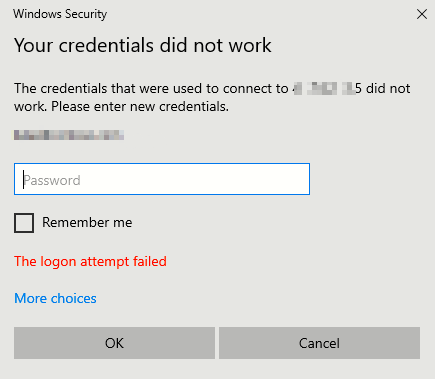
Issue #1: The Login Attempt Failed
When running the “az network bastion rdp” command it is possible that you will be presented with the below error.
Resolution
- Run the following command
az network bastion rdp --name "name of bastion resource" --resource-group "name of resource group where bastion resource lives" --target-resource-id "the full resource ID of the VM that you would like to connect to" --enable-mfaThe key here is to include the following optional switch at the end:
--enable-mfa- A Microsoft prompt will appear for you to login as the Entra user. Enter the credentials as normal. Without the –enable-mfa switch, this prompt would not appear.
Issue #2: Unable to Change Entra User
Once you use the –enable-mfa switch and authenticate to the VM using Bastion, the credentials get stored, and you’re unable to login as a different user moving forward. This is highly inconvenient! The Entra credentials are not stored in the Windows Credential manager either. What happens if you want to log in as a different Entra user? Please see resolution below.
Resolution
You need to add the –configure optional switch, as per below:
az network bastion rdp --name "name of bastion resource" --resource-group "name of resource group where bastion resource lives" --target-resource-id "the full resource ID of the VM that you would like to connect to" --enable-mfa --configureThe –configure switch will open the RDP client where you will get the option to provide a different username.