Issue
When you are tasked with troubleshooting network connectivity issues with Azure Firewall, network rule log data should be one of the first places to inspect. By default, the logs do not tell you which rule or policy each event is paired with. This can cause delays during the troubleshooting process when you need to work out whether a particular rule is functioning or not.
When inspecting network rule log data, you will be presented with N/A:
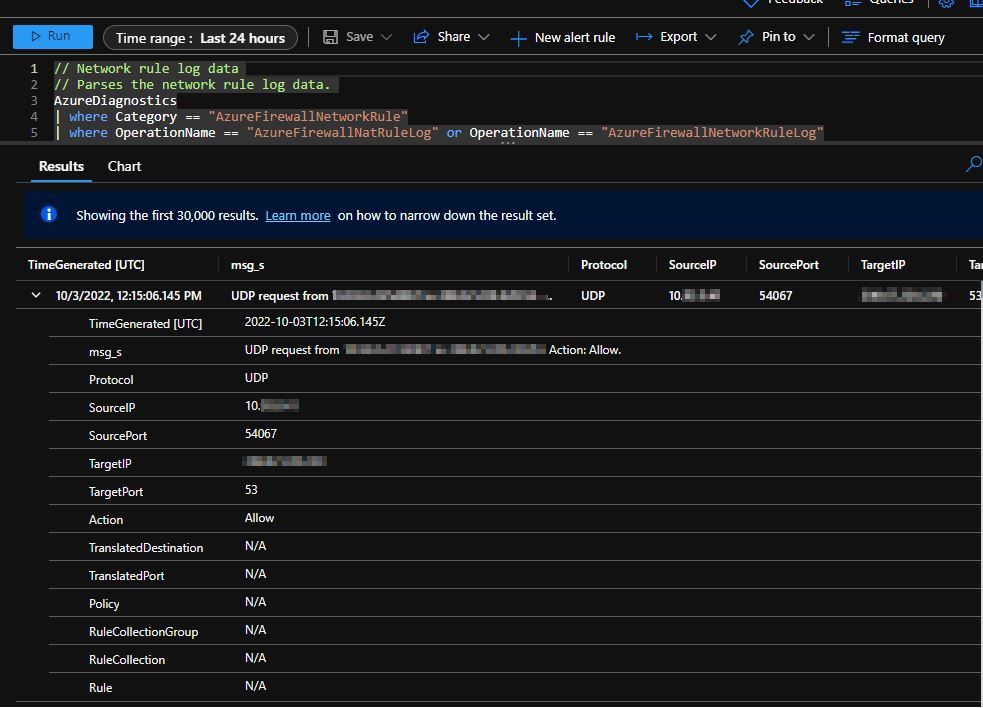
Resolution
Microsoft allow you to view network rule names in Azure Firewall logs, but it is currently a feature that is in preview. To enable this function, please follow below instructions:
1. Run the below Azure PowerShell commands:
Connect-AzAccount
Select-AzSubscription -Subscription "subscription_id or subscription_name"
Register-AzProviderFeature -FeatureName AFWEnableNetworkRuleNameLogging -ProviderNamespace Microsoft.Network
Register-AzResourceProvider -ProviderNamespace Microsoft.Network2. Once the commands have been processed, it will not take effect immediately. You must run an operation on the Firewall. The easiest way to do this is to either add or update an existing rule. If you don’t, it can take several days for the feature to enable.
3. Check the Network rule log data to confirm the change has taken place. You should now be able to see the rule name in an event:
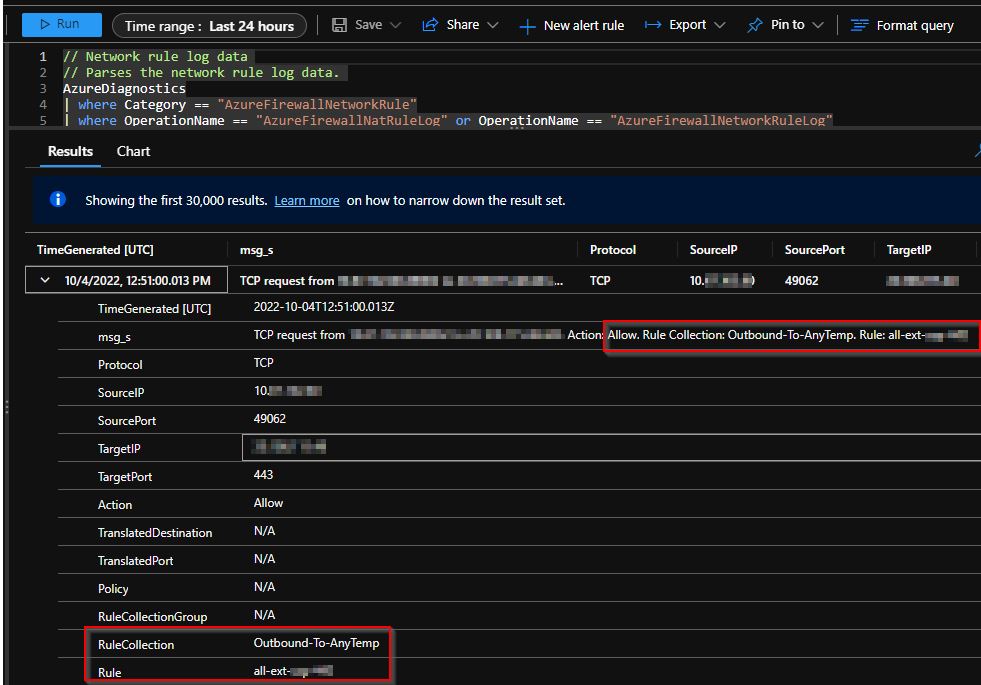
Hopefully, this will be integrated within Azure Firewall by default in the near future.

