Introduction
When it comes to protecting web traffic, it can be difficult to identify the best method of protecting connectivity. Azure Application Gateway can be placed before Azure Firewall. Inbound web traffic goes through both resources to offer more protection. Web traffic firstly hits the application gateway, then the traffic is forwarded to the firewall. Azure firewall will do its job and inspect traffic between application gateway and the backend pool.
For organisations that require full auditing and logging of inbound web data, then this is a good topology to deploy. The below table is a summary of the traffic flow supported by this topology:

This post will walk through the steps required to set up and configure Application Gateway before Azure Firewall.
Scenario
Here is the scenario we will be deploying:
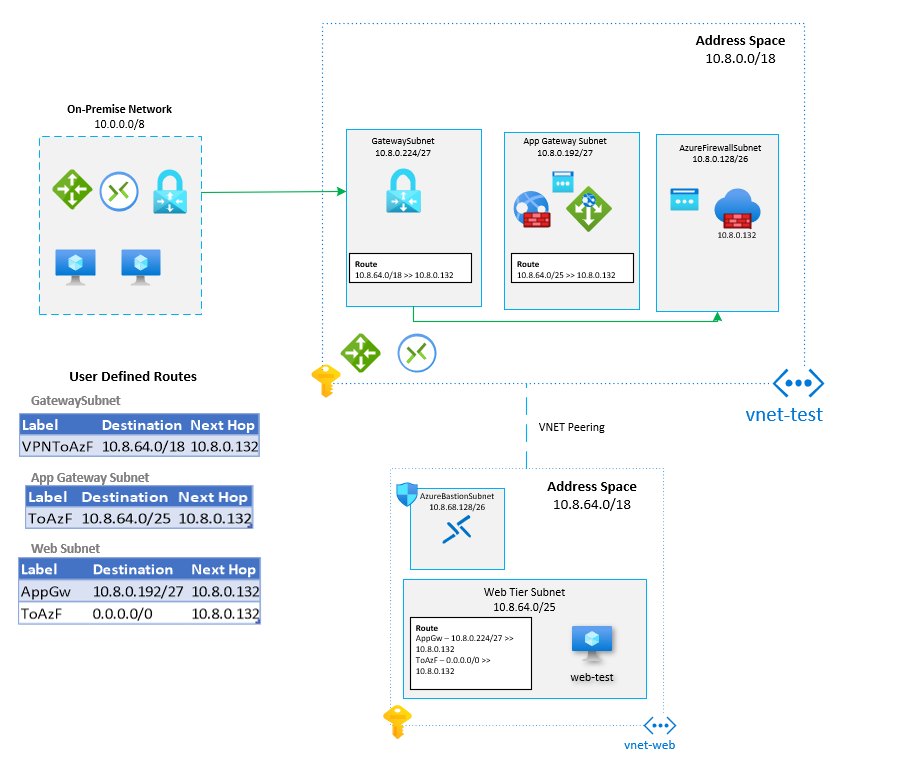
To test the configuration, a web-test VM has been placed in the Web Tier subnet. The VM will be used to demonstrate http routing from the Application Gateway. This guide assumes that the on-premises site-to-site VPN has already been configured. The configuration of a site-to-site VPN tunnel won’t be covered in this post. Only HTTP traffic will be tested and demonstrated in this scenario.
Create Virtual Networks
Two new virtual networks will need to be created to support the architecture. One will be the Hub network (vnet-test), where Application Gateway and Firewall will be deployed. The second will be a spoke network (vnet-web) where the Web tier will be configured.
Hub VNET Settings:


VNET peering will also need to be configured between the two virtual networks:


Deploy Application Gateway
Once the VNETs have been configured, the application gateway can be deployed and configured.
- In Azure marketplace, search for application gateway:

- Click on Create.
- Give the App Gateway a name and choose WAF V2:

- Assign the VNET and AppGWSubnet which was created in the VNET section:

- Assign a public and private IP address for the application gateway:

- Configure the backend pool and enter the private IP address of the web-test VM as the target.

- Configure a Routing Rule to enable the listener on port 80:

- Click on Backend Targets and choose the backend pool that was created in step 6, also and a new http setting:


- Review and create the Application Gateway.
Deploy Azure Firewall
- In Azure Marketplace search for Firewall:

- Click on Create.
- Create a new Firewall policy:

- Select vnet-test (where the AzureFirewallSubnet was configured):

Configure Route Tables
User Defined Routes (UDRs) will plug all the plumbing together. Please refer to the architecture diagram at the start of this post to see which UDRs will be configured.
- In Azure Marketplace search for Route Table:

- Create Route Table and call it “AppGateway-Route”:

- Review and create.
- Repeat above steps but create two different route tables called: GatewaySubnet-Route and WebSubnet-Route.
- Navigate to the AppGateway Route and create a route:

- Navigate to vnet-test and assign the newly created route to the AppGW subnet:

- Navigate to the WebSubnet-Route table and create a new route called “AppGw”, this will ensure traffic destined to the application gateway will be filtered via Azure firewall:

- Create a second route to direct all internet traffic to Azure Firewall:

- Apply the new route table to the web subnet:

- Create a new route in the GatewaySubnet-Route route table. The traffic destined for 10.8.64.0/18 will need to go via the Azure Firewall (10.8.0.132).
- Apply the GatewaySubnet-Route route table to the GatewaySubnet.
Azure Firewall Rule
Finally, an Azure Firewall rule will need to be created to accept traffic from the Application Gateway subnet to the Web subnet via port 80 (http). To set this up, create a network rule in Azure Firewall:

Test Connectivity
The web-test VM has IIS installed to demonstrate connectivity. To test whether Application Gateway is working as expected, open up a web browser and load the public IP address of the Application Gateway:

Azure Firewall will now analyse traffic between application gateway and the backend pool!
Wrap Up
The post demonstrated the power of using Application Gateway and Azure Firewall together to offer further protection against attacks. Azure Firewall is an integral component in this scenario as it acts as a central logging and auditing repository. To analyse logs, a log analytics workspace must be created. Furthermore, the Azure Firewall Diagnostic settings will need to be linked to the workspace. This is something I may cover in a future post.
The documentation on Microsoft’s site is lacking when it comes down to the low-level deployment steps for this scenario. Hopefully, this guide has helped with configuring application gateway before firewall. 👍

Hi, there thanks for the detailed document it’s really helpful.
I would like to know if the Gateway subnet is part of the Web Application Gateway or is this because of the VPN setup you have, I am not sure if I need to exclude this or not ?
Thanks
Hi,
In the given scenario, the gateway subnet purely relates to the Site-to-Site VPN tunnel between the on-premises network and Azure. I hope this helps.
Thanks
Hi, please could you confirm if both the Application gateway and firewall are in the same resource group?